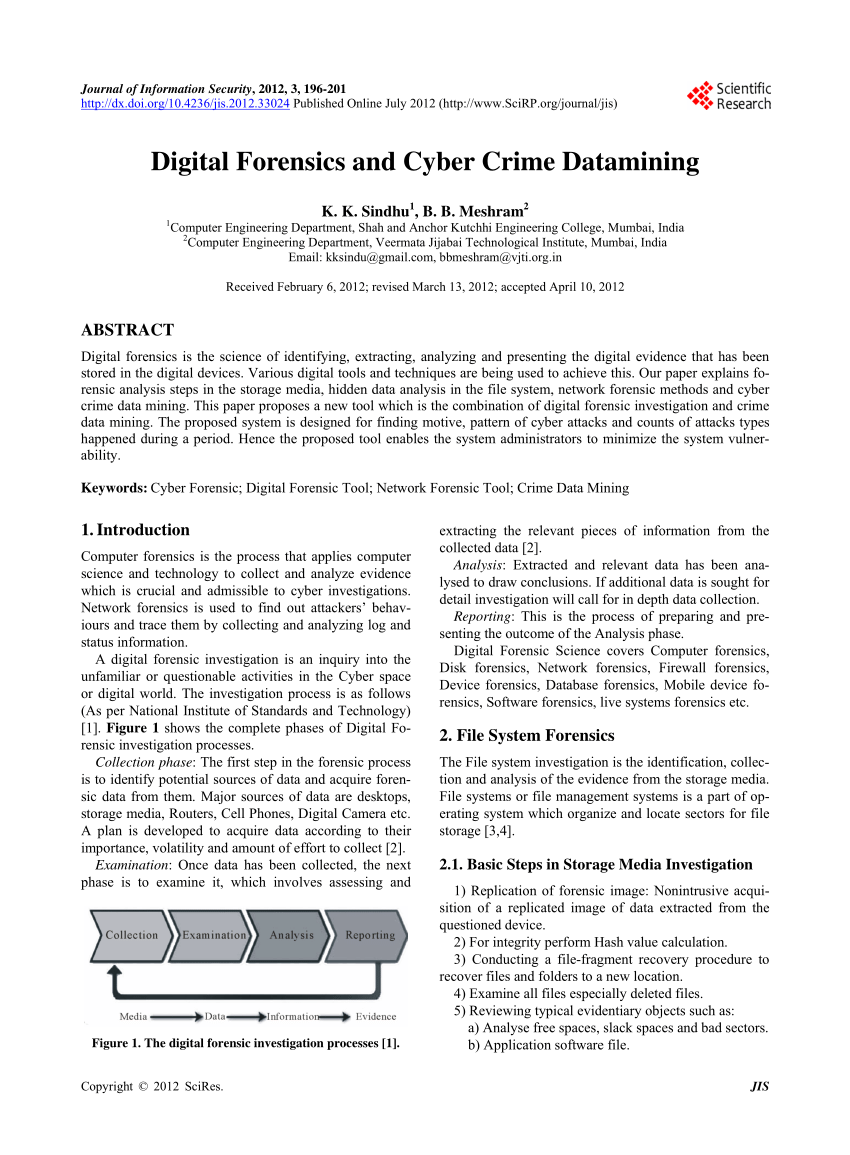
- Computer Forensics For Beginners
- Computer Forensics And Investigations Pdf
- A Practical Guide To Computer Forensics Pdf
- Computer Forensics Book Pdf
- Digital Forensics Pdf
- Guide To Computer Forensics Pdf Editing
Computer forensics is a relatively new discipline to the courts and many of the existing laws used to prosecute computer-related crimes, legal precedents, and practices related to computer forensics are in a state of flux. This publication is intended to help organizations in investigating computer security incidents and troubleshooting some information technology (IT) operational problems by providing practical guidance on performing computer and network forensics. The guide presents forensics.
26 Nov What is Computer Forensics?
About this guide
This guide talks about computer forensics from a neutral perspective. It’s not linked to particular legislation or intended to promote a particular company or product, and it’s not biased towards either law enforcement or commercial computer forensics.
Rather, it aims to give the non-technical reader a high-level view of computer forensics. We use the term ‘computer’, but the concepts apply to any device capable of storing digital information. Where we mention particular methods, they are intended only as examples, not recommendations or advice.
If you copy any content from this page, please credit and link back to https://forensiccontrol.com.
Thank you.
When and how is computer forensics used?
There are few areas of crime or dispute where computer forensics cannot be applied. Law enforcement agencies were among the earliest and heaviest users of computer forensics – as a result they’ve often been at the forefront of developments in the field.
Computers can be considered a ‘scene of a crime’ – for example with hacking or denial of service attacks. They may hold evidence of crimes that happened elsewhere, in the form of emails, internet history, documents or other files relevant to crimes such as murder, kidnap, fraud or drug trafficking.
A forensic computer exam can reveal more than expected
Investigators are not only interested in the content of emails, documents and other files, but also in the metadata associated with those files. Records of a user’s actions may also be stored in log files and other applications on a computer, such as internet browsers.
So a computer forensic examination might reveal when a document first appeared on a computer, when it was last edited, when it was last saved or printed and which user carried out these actions.
Commercial organisations have used computer forensics to help with all kinds of cases, including:
- Intellectual Property theft
- Employment disputes
- Invoice fraud, often enabled by phishing emails
- Forgeries
- Inappropriate email and internet use in the workplace
- Regulatory compliance
Guidelines for successful computer forensics
If evidence found during a computer forensic investigation is to be admissible, it must be reliable and ‘not prejudicial’. This means the examiner needs to keep admissibility at the front of his mind at every stage of an investigation.
The U.K.’s Association of Chief Police Officers’ Good Practice Guide for Digital Evidence – or ACPO Guide – is a widely used and respected set of guidelines for investigators. ACPO has now become the National Police Chief’s Council. The guide has not been updated for several years but its content remains relevant; the technologies change but the principals remain constant.
The four main principles from the APCO Guide
Please note references to law enforcement have been removed.
- No action should change data held on a computer or storage media which may be subsequently relied upon in court.
- In circumstances where a person finds it necessary to access original data held on a computer or storage media, that person must be competent to do so and be able to give evidence explaining the relevance and the implications of their actions.
- An audit trail or other record of all processes applied to computer-based electronic evidence should be created and preserved. An independent third-party should be able to examine those processes and achieve the same result.
- The person in charge of the investigation has overall responsibility for ensuring that the law and these principles are adhered to.
Live acquisition: Getting data from a powered computer
So, are there instances when a computer forensic examiner might need to make changes to a suspect’s computer and – in doing so – go against principle No.1 above? Yes.
Traditionally, examiners copy data from a device which is turned off. They use a write-blocker to make an exact bit for bit copy of the original storage medium, and create an acquisition hash of the original medium. Then they work from this copy, leaving the original obviously unchanged.
However, sometimes it’s not possible (or desirable) to switch off a computer. Perhaps doing so would result in considerable financial or other loss for the owner, or cause valuable evidence to be permanently lost. In these cases, the computer forensic examiner may need to carry out a ‘live acquisition’. This involves running a simple application on the suspect computer to copy (acquire) the data to the examiner’s data repository.
By running such an application (and attaching a device such a USB drive to the suspect computer), the examiner makes changes and/or additions to the computer which were not present before. But if the examiner records these actions, can show why they were necessary, and explain their consequences to a court, the evidence produced is usually still admissible.
The stages of a computer forensics examination
The process is divided into six stages.
1. Readiness
Forensic readiness is an important and occasionally overlooked stage in the process. In commercial computer forensics, it might include educating clients about system preparedness. For example, forensic examinations provide stronger evidence if a device’s auditing features are activated before an incident takes place.
For the forensic examiner, readiness includes appropriate training, testing and verification of their own software and equipment. They need to be familiar with legislation, know how to deal with unexpected issues (such as what to do if child abuse images are found during a fraud engagement) and ensure their data acquisition computer and associated items are suitable for the task.
2. Evaluation
During the evaluation stage, the examiner receives instructions and seeks clarification if any of these are unclear or ambiguous, carries out risk analysis and allocates roles and resources. For law enforcement, risk analysis might include assessing the likelihood of physical threat on entering a suspect’s property and how best to deal with it.
Walter mitty character. Commercial organisations also need to consider health and safety issues, conflict of interest issues and possible risks – financial and to their reputation – when they accept a particular project.
3. Collection
If data acquisition (often called ‘imaging’) is carried out on-site rather than at the computer forensic examiner’s office, this stage includes identifying and securing devices which may store evidence, and documenting the scene.
The examiner would also hold interviews or meetings with personnel who might have information relevant to the examination – such as the computer’s end-users, the manager and the person responsible for computer services, i.e. an IT administrator.
The collection stage can also involve the labelling and bagging of items from the site which may be used in the investigation – these are sealed in numbered tamper-evident bags. The material then needs to be securely and safely transported to the examiner’s office or laboratory.
4. Analysis
Analysis includes the discovery and extraction of information gathered in the collection stage. The type of analysis depends on the needs of each case. It can range from extracting a single email to piecing together the complexities of a fraud or terrorism case.
During analysis the examiner usually feeds back to their line manager or client. These exchanges may result in the analysis taking a different path or narrowing to specific areas. Forensic analysis must be accurate, thorough, impartial, recorded, repeatable and completed within the available timescales and allocated resources.
Computer Forensics For Beginners
There are multiple tools available for computer forensics analysis. The examiner should use any tool they feel comfortable with, as long as they can justify their choice. A computer forensic tool must do what it’s meant to do, so examiners need to regularly test and calibrate their tools before carrying out any analysis.
Computer Forensics And Investigations Pdf
Examiners can also use ‘dual-tool verification’ to confirm the integrity of their results during analysis. For example, if the examiner finds artefact X at location Y using tool A, they should be able to replicate these results with tool B.
5. Presentation
In this stage the examiner produces a structured report on their findings, addressing the points in the initial instructions, along with any further instructions they have received. The report should also cover any other information the examiner deems relevant to the investigation.
The report must be written with the end reader in mind. Often that the reader will be non-technical, so appropriate terminology should be used. The examiner may need to participate in meetings or conference calls to discuss and elaborate on their report.
6. Review


Like the Readiness stage, the Review is often overlooked or disregarded, because it’s not billable work or because the examiner needs to get on with the next job. But carrying out a review of each examination can make future projects more efficient and time-effective, which saves money and improves quality in the longer term.
The review of an examination can be simple, quick and begin during any of the above stages. It could include a basic analysis of what went wrong and what went well, along with feedback from the person/company who requested the investigation. Any lessons learnt from this stage should be applied to future examinations and feed into the Readiness stage.
What issues do computer forensics examiners face?
Computer forensics examiners come up against three main categories of problem: technical, legal and administrative.
Technical issues
Encryption
Encrypted data can be impossible to view without the correct key or password. If the key isn’t available or the owner won’t reveal it, it may be stored:
- elsewhere on the computer
- on another computer which the suspect can access
- on the computer’s volatile memory (RAM). This is usually lost on computer shut-down
When encryption may be present the examiner may need to consider using the ‘live acquisition’ techniques outlined above.
A Practical Guide To Computer Forensics Pdf
Increasing storage space
Storage media hold ever-greater amounts of data, so the examiner’s analysis computers need sufficient processing power and available storage capacity to search and analyse large amounts of data efficiently.
New technologies
Computing is a continually evolving field, with new hardware, software and operating systems emerging constantly. No single computer forensic examiner can be an expert on all areas, though they are often expected to analyse something they haven’t encountered before.
This means they need to be prepared and able to test and experiment with the behaviour of new technologies. At this point, networking and sharing knowledge with other computer forensic examiners comes in useful, because someone else may already have come across the same issue.
Anti-forensics
Anti-forensics is the practice of attempting to thwart computer forensic analysis – through encryption, over-writing data to make it unrecoverable, modifying files’ metadata and file obfuscation (disguising files). As with encryption, the evidence that such methods have been used may be stored elsewhere on the computer or on another computer which the suspect can access.
In our experience, it’s very rare to see anti-forensics tools used correctly and frequently enough to totally obscure their presence or the presence of the evidence they were used to hide.
Legal issues
Legislative domains – Data often isn’t stored on a person’s computer but on remote computers which they are renting storage space on, otherwise known as the ‘cloud’. This data may be in a different country, meaning access to it could involve different legislation. And if access is possible, it may be complicated and expensive.
Legal arguments – Legal issues can confuse or distract from a computer examiner’s findings. One example of this is the ‘Trojan Defence’. A Trojan is a piece of computer code disguised as something benign but which has a hidden and malicious purpose. Trojans have many uses, including key-logging, up/downloading files and installing viruses.
A lawyer may be able to argue that actions on a computer were not carried out by a user, but instead automated by a Trojan without the user’s knowledge. This kind of Trojan Defence has been successfully used even when no trace of a Trojan or other malicious code was found on the suspect’s computer. Utorrent free download pc.
Computer Forensics Book Pdf
In such cases, a competent opposing lawyer supplied with evidence from a competent computer forensic analyst should be able to dismiss the argument. A good examiner will have identified and addressed possible arguments from the ‘opposition’ during the analysis and writing stages of their report.
Administrative issues
Accepted standards –
There are all kinds of standards and guidelines in computer forensics, few of which are universally accepted. The reasons for this include:
- Standard-setting bodies can be tied to particular legislations
- Standards are aimed either at law enforcement or commercial forensics but not both
- The authors of such standards are not accepted by their peers
- High joining fees for professional bodies can put practitioners of
Fit to practice – Many jurisdictions have no qualifying body to check the competence and integrity of computer forensics professionals. This means anyone can present themselves as a computer forensic expert, which in turn can lead to poor quality examinations and a negative view of the profession as a whole.
At Forensic Control we are experts in Computer Forensics so if you need any assistance please just drop us a message and we will be happy to advise. You can book a computer investigation with one of our examiners. Alternatively, if you’re in the UK we can also help you with cyber essentials.
Resources and further reading
Most resources about computer forensics are aimed at tech-minded readers, but you might find the following links useful:
- Forensic Focus This excellent resource has a popular message board and lists training courses in various locations
- NIST Computer Forensic Tool Testing Program This National Institute of Standards and Technology (America) industry-respected programme enables tool testing to ensure they consistently produce accurate and objective test results
- Computer Forensics World A CF community web site with message boards
- First Forensic Forum (F3) This UK-based non-profit organisation organises workshops and training for forensic computing practitioners
Glossary | A guide to computer forensics terms
Acquisition hash: the result of an algorithmic calculation which produces a unique string of characters that act as a digital “fingerprint” for a particular data set

Bit copy: ‘bit’ is a contraction of the term ‘binary digit’ and is the fundamental unit of computing. A bit copy refers to a sequential copy of every bit on a storage medium, which includes areas of the medium ‘invisible’ to the user.
Denial of Service attack: an attempt to prevent legitimate users of a computer system from having access to that system’s information or services.
Hacking: modifying a computer in a way which was not originally intended in order to benefit the hacker’s goals.
Key-logging: the recording of keyboard input giving the ability to read a user’s typed passwords, emails and other confidential information.
Metadata: data about data. It can be embedded within files or stored externally in a separate file and may contain information about the file’s author, format, creation date and so on.
Digital Forensics Pdf
Phishing: attempts to trick users into doing ‘the wrong thing’, such as clicking a bad link that will download malicious software, or direct them to a website which will trick them into supplying their password.
Guide To Computer Forensics Pdf Editing
RAM: Random Access Memory. RAM is a computer’s temporary work space and is volatile, which means its contents are lost when the computer is powered off.
Write blocker: a hardware device or software application which prevents any data from being modified or added to the storage medium being examined.